Sniffing Various Passwords Via MITM with DSNIFF and SSL Strip
Dsniff: All your plaintext passwords are belong to us
=====================================================
For anyone not familiar you can check over in the Tools DB for some brief info linked below.
http://www.soldierx.com/tools/Dsniff
This app very well displays the inherent security risk of paintext traffic.
Note: The web page still reports 2.3 as latest, but 2.4 is in BT4 Final its apparently beta as of writing.
What types of passwords does Dsniff recognize?
==============================================
Per wiki: FTP, Telnet, SMTP, HTTP, POP, poppass, NNTP, IMAP, SNMP, LDAP, Rlogin, RIP, OSPF, PPTP MS-CHAP, NFS, VRRP, YP/NIS, SOCKS, X11, CVS, IRC, AIM, ICQ, Napster, PostgreSQL, Meeting Maker, Citrix ICA, Symantec pc Anywhere, NAI Sniffer, Microsoft SMB, Oracle SQL*Net, Sybase and Microsoft SQL protocols
You'll need the following:
==========================
1 machine for traffic generation
1 for MITM injection of ARP ( Im using bt4 final )
1 A machine hosting plain text services ( or use the gateway in the attack and test with web )
A quick note or 2 on ARP spoofing:
==================================
It's very important to note that a slow machine will *greatly* reduce network throughput with this type of attack depending on traffic. If you spoof a whole subnet and aren't careful you can create a DOS condition or severe latency. For initial testing start SMALL! If you are running this somewhere you shouldn't be (you guys promise not to right!?) you can really get noticed quickly.
It's also fairly easy to spot a whole subnet being spoofed in a matter of seconds with tcpdump or wireshark on affected machines.
*Change your MAC gentlemen*
Something else to consider is your network type and implementation. This will work on WEP/WPA networks, wpa has some issues by design with sniffing so I've heard, but this MITM should mitigate most of the issues.
Switched Ethernet networks are really the most ideal condition.
On a hub network, you will SEVERELY crappify everyones connections due to the multitude of additional collisions you are creating. Also, you don't need to spoof it anyway, all the traffic is already coming to your port.
I mention this specifically because I have seen several businesses implement a tiered network with switches a a backbone and hubs hung off them because they are too cheap to buy individual network drops.
Additionally, as you will see, there's more than one app to use for arp spoofing, you can use arpspoof or ettercap depending on what options you need, there are likely others too.
Down to Business:
=================
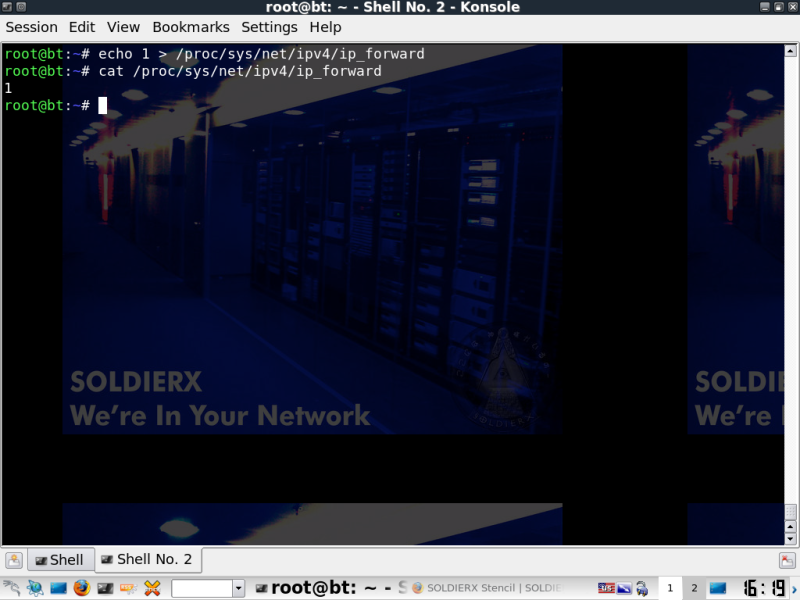
Enable IP forwarding, or you will IMMEDIATELY DOS EVERYONE IN YOUR WAKE!
-For anyone interested if you don't enable forwarding, you will receive the response packets and simply not do anything with them, therefore the traffic will fail.
echo 1 > /proc/sys/net/ipv4/ip_forward (This simply changing the value of the file from 0 to 1)
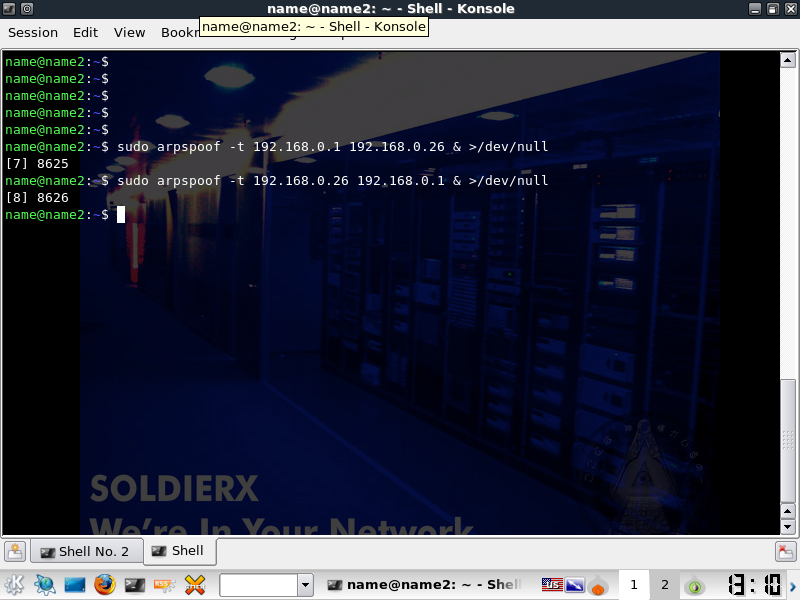
Now you should check out the easy usage for arpspoof.
arpspoof -h
Now that you *hopefully* understand the usage, pick a target and its destination that you want to spoof.
This is usually the default gateway for your host, and the host if you are trying to get the most traffic.
Before you launch anything, you should know that by default you will get tons and tons of info for each packet sent to the screen. As noted over on the Irongeek (link at bottom), you can simply pipe it to /dev/null if you don't want to see it by adding & >/dev/null to the end of the command.
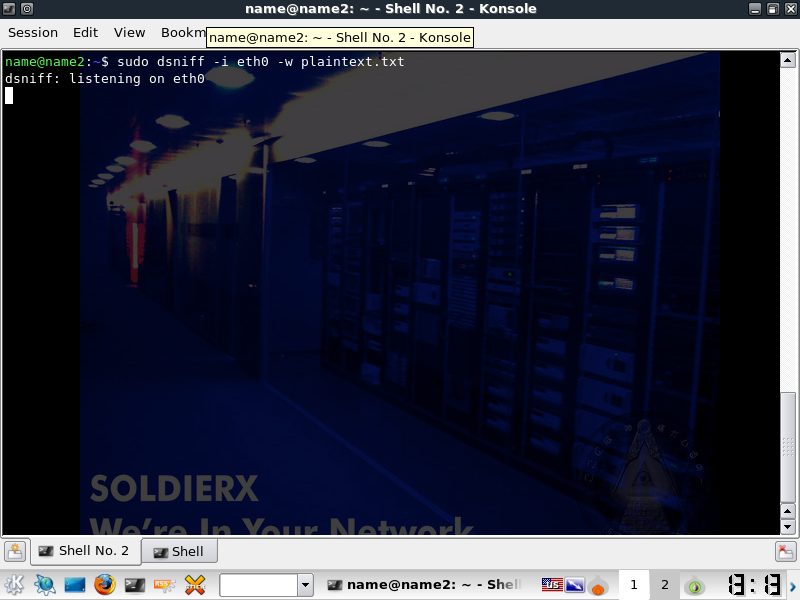
Launch Dsniff
If you want to only select certain services you will need to add the -f flag. -w will write the passwords to file.
dsniff -i -w plaintext.txt
You're now sniffing traffic from your target(s) test or wait for the traffic. If you didn't enable Ip forwarding earlier, the targets are down.
At this point, you are sniffing *Plaintext Passwords*. To take the attack to the next level and start pulling out SSL + HTTPS you could use the following. -a is SSL & HTTPS traffic -w is once again write to file.
sslstrip -a -w encrypted.txt
Once you have the basics of arp spoofing down, you just need to look into the various services you want to sniff or modify.
73's
For More info on sniffing and some other approaches across other platforms:
http://www.irongeek.com/i.php?page=security/AQuickIntrotoSniffers